Centralize all Mailinblack cybersecurity solutions in a single platform

Reduce your risk of being attacked with our cybersecurity solutions
Protect, educate, train: the winning triptych for your cybersecurity
Mailinblack solutions are a combination of technological innovations that allow you to secure your organization and educate and train your employees against cyber attacks. Let’s find them on the Mailinblack platform.
Strengthen your security and gain productivity and peace of mind with our AI
Our Protect solution implements an advanced filtering of emails before they are received. Our proprietary AI defuses phishing, spearphishing and ransomware attacks and keeps your teams focused on their legitimate emails.
Coach your employees like a high performance team
Audit your organization and implement a 100% automated attack simulation program with Cyber Coach, the most complete cybersecurity awareness solution on the market.
Train your teams in cybersecurity with a complete and fun solution
Cyber Academy is based on the 4 pillars of learning: attention, active engagement, return on error and consolidation. Our e-learning platform offers your employees a complete and fun educational experience in cybersecurity training.
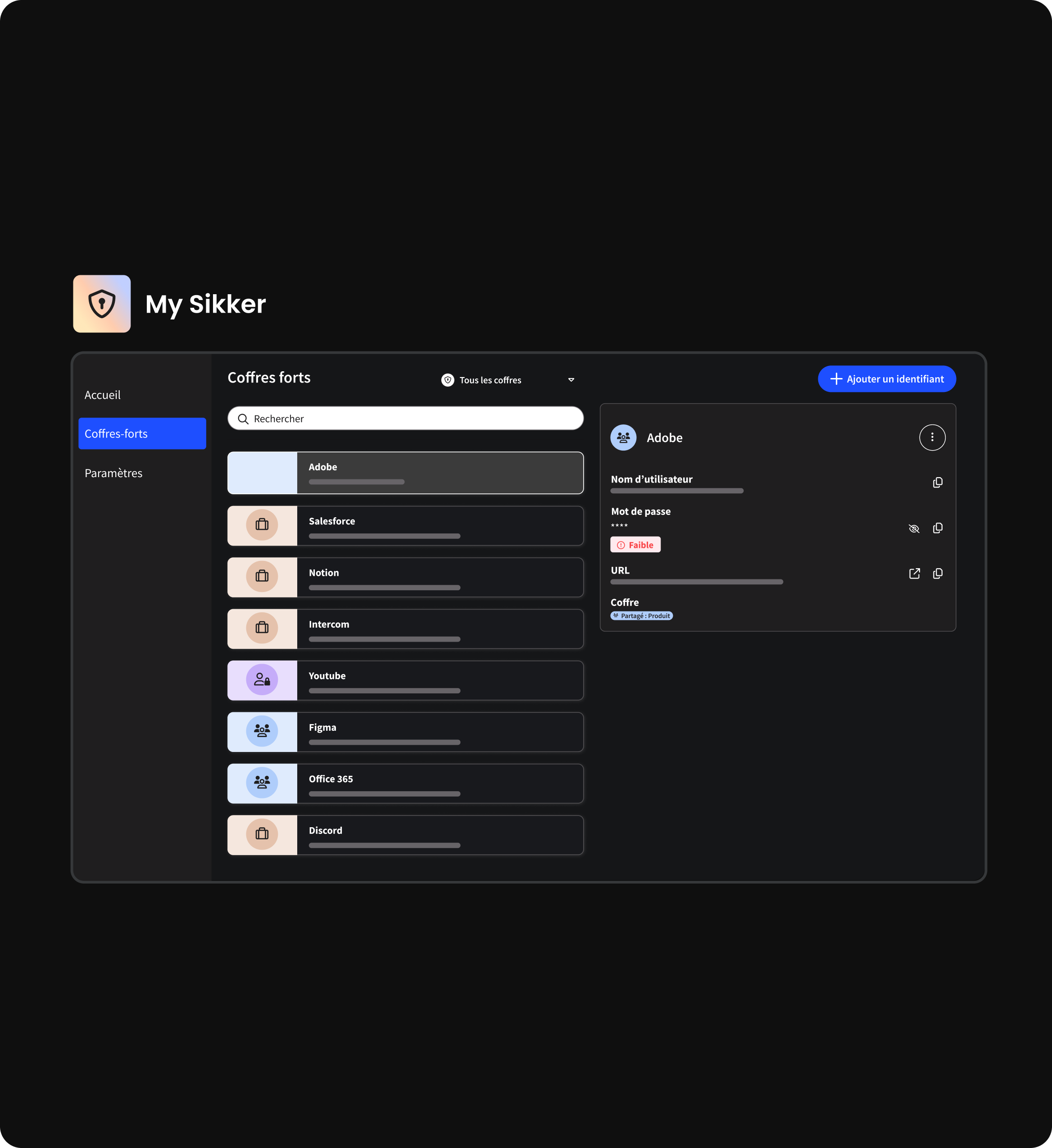
Simplify password management within your organization
Sikker transforms the concept of digital security by combining ease of use with robust protection, without making any concessions. With its password manager for enterprises, it provides centralized access management and integrates advanced security features, offering complete peace of mind.
Engage your teams in your company’s cybersecurity to achieve higher levels of digital protection.